
A group of computer scientists at the Massachusetts Institute of Technology (MIT) has developed a new SMS text messaging system, dubbed Vuvuzela, that is untraceable and could allow truly anonymous communications.
The researchers explained that their SMS text messaging system is resilient to traffic analysis, so more secure than the Tor anonymity network.
“Tor operates under the assumption that there’s not a global adversary that’s paying attention to every single link in the world,” said Nickolai Zeldovich, an associate professor of computer science and engineering, and co-leader of the Parallel and Distributed Operating Systems group at CSAIL.
“Maybe these days this is not as good of an assumption. Tor also assumes that no single bad guy controls a large number of nodes in their system. We’re also now thinking, maybe there are people who can compromise half of your servers.”
Scientists from MIT and the Qatar Computing Research Institute (QCRI), in July, claimed to be able to de-anonymize Tor hidden servers with up to 88% accuracy. The researcher demonstrated how to unmask Tor hidden services in the Tor Network by analyzing the traffic patterns of encrypted data passing through a single machine in the Tor network.
The researchers demonstrated that “simply by looking for patterns in the number of packets passing in each direction through a guard, machine-learning algorithms could, with 99 percent accuracy, determine whether the circuit was an ordinary Web-browsing circuit, an introduction-point circuit or a rendezvous-point circuit.”
“Furthermore, by using a Tor-enabled computer to connect to a range of different hidden services, they showed that a similar analysis of traffic patterns could identify those services with 88 per cent accuracy. That means that an adversary who lucked into the position of guard for a computer hosting a hidden service, could, with 88 per cent certainty, identify it as the service’s host.” States the MIT’s full press release .”
In October, the researchers presented their paper, titled “Vuvuzela: Scalable Private Messaging Resistant to Traffic Analysis” at the Association for Computing Machinery Symposium on Operating Systems Principles.
“Vuvuzela is a new scalable messaging system that offers strong privacy guarantees, hiding both message data and metadata. Vuvuzela is secure against adversaries that observe and tamper with all network traffic, and that control all nodes except for one server” states the paper.
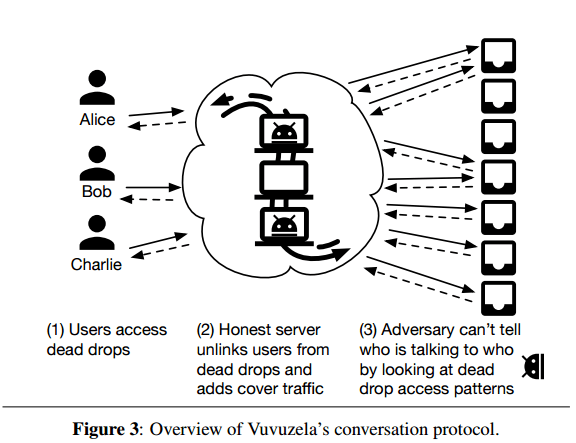
A user that needs to send a message to another user leaves it at a specific location, such as a memory address on an internet-connected dead drop server, then its interlocutor retrieves the message from the same location.
In the simplest scenario were three people using the system but only two of them were sending text messages to each other, an attacker that analyze the traffic to the server is able to track the two users that exchanged messages.
To avoid traffic analysis in this scenario, the users, even not involved in any communication, send out regular messages to the dead-drop server making ineffective traffic analysis.
In this case, a persistent attacker running a traffic analysis will be only able to see traffic going through the server from multiple locations at all times.
The researchers explained that sending out regular spoof messages is not enough to avoid traffic analysis due to the possibility that an attacker can infiltrate the dead-drop server. In this case, the attacker would be able to see which users were actually sending out messages and who is its interlocutor.
To make the Vuvuzela resilient to this kind of attack, the SMS text messaging system uses three different dead drop servers.
All the messages, real and fake, are sent through the system wrapped in three layers of encryption.
” To make sure that exchange requests get mixed, each client encrypts their request with the public key of each server. If there are three servers, with public keys pk1, pk2, and pk3, then a user encrypts their request r to form Epk1 (Epk2 (Epk3 (r))). 5 This onion construction ensures that the request r can be decrypted only if each server removes its encryption layer in turn” states the paper.
The first server peels off the first layer of encryption on a message and then forward it to the second server. The first server also mixes up the order of the messages, and the second server does the same, so the third server is the unique one that can read the real messages.
The three layers of encryption allow the Vuvuzela SMS text messaging system to be effective even if one of the server is compromised.
(Security Affairs – Vuvuzela, SMS text messaging system)