
The tool was developed to facilitate and speed up the process of finding and downloading malware samples via the command line interface.
We’ve made use of the API provided by the two major malware dump sites (openmalware.org and malwr.com) in a script that’s simple and pretty straightforward, which allows users to query information pertaining to malware, such as: Name, MD5, SHA-1, SHA-256, download the desired malware sample file, and even compare its digital signature (hash) with the ones present in the dumps in question.
Our next mission is to pull off the same deed, this time, however, using malwr.com, MalShare, MalwareBlacklist, Malware.lu’s AVCaesar from command line malware samples submission, to hash comparison and research.
Video:
Optional Arguments:
$ Malwaresearch.py [--h HELP] [-f FIND] [-w WRITE]
[-o OUTPUT] [-d DOWNLOAD] [-hash HASH
-h,HELP, --help Show this help message and exit
-f FIND, --find Enter your search via NAME, MD5, SHA1, SHA256 or an Common Signature name.
-w WRITE, --write Save this result on file
-o OUTPUT, --output Max numbers of malwares search
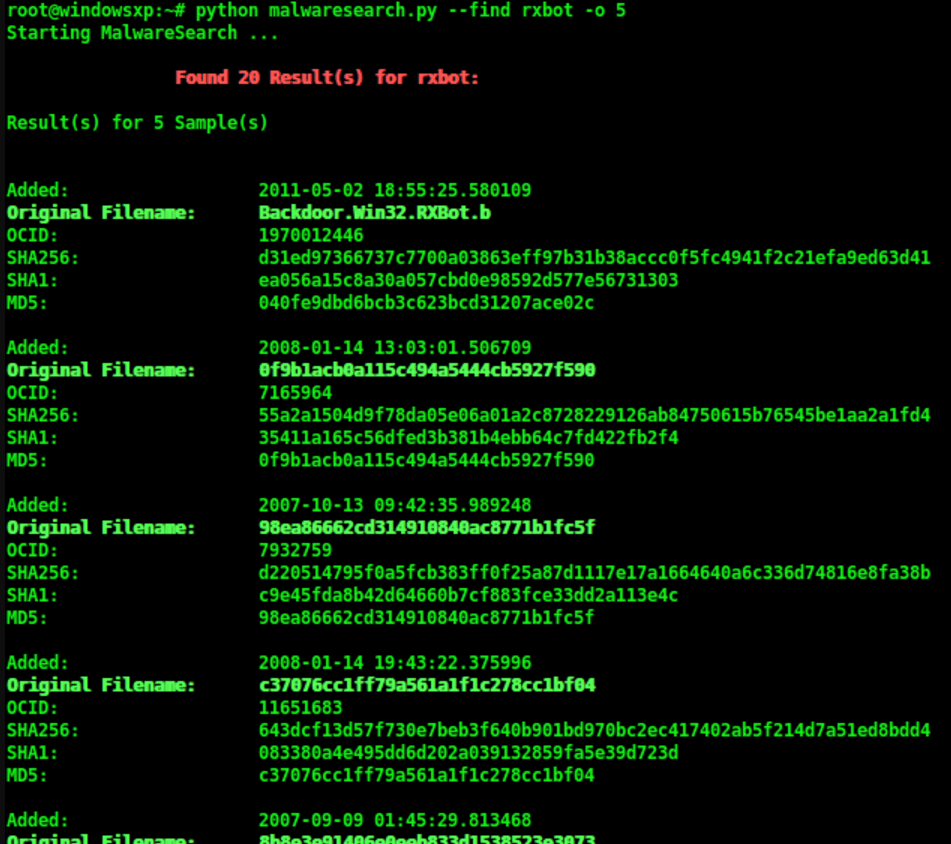
-d DOWNLOAD, --download Download your specific malwareExample to find rxbot samples:
About the author: Ialle Teixeira
Information Security and Malware Researcher, Core of Malware Reverse Brazil( Articles and live reverse engineering and malware analysis classes)
[adrotate banner=”9″]
(Security Affairs – malware, Malwaresearch)
[adrotate banner=”13″]