
The security expert Orange Tsai from the DevCore firm has found a malicious web shell on Facebook Server. The researcher was analyzing the Facebook’s infrastructure when noticed a domain called files.fb.com. Intrigued, the expert has tried to access the domain discovering that it was hosting an instance of the Accellion File Transfer Appliance that is used by companies or secure file transfers.
Once accessed the domain it displayed a login interface for the File Transfer Appliance then he decided to investigate the presence of security vulnerabilities in the software.
He verified that Facebook already fixed known flaw in the software then he decided to search for new security issues in the appliance. Tsai discovered a total of 7 zero-day flaws, including cross-site scripting, remote code execution, and local privilege escalation vulnerabilities.

He exploited a pre-auth SQL injection flaw to upload a webshell to the Facebook server and gain its control. At this point, he noticed something of really strange, someone had anticipated him by uploading a webshell to the server.
“While collecting vulnerability details and evidences for reporting to Facebook, I found some strange things on web log. First of all I found some strange PHP error messages in “/var/opt/apache/php_error_log” These error messages seemed to be caused by modifying codes online?” wrote Tsai. “I followed the PHP paths in error messages and ended up with discovering suspicious WEBSHELL files left by previous “visitors”.”
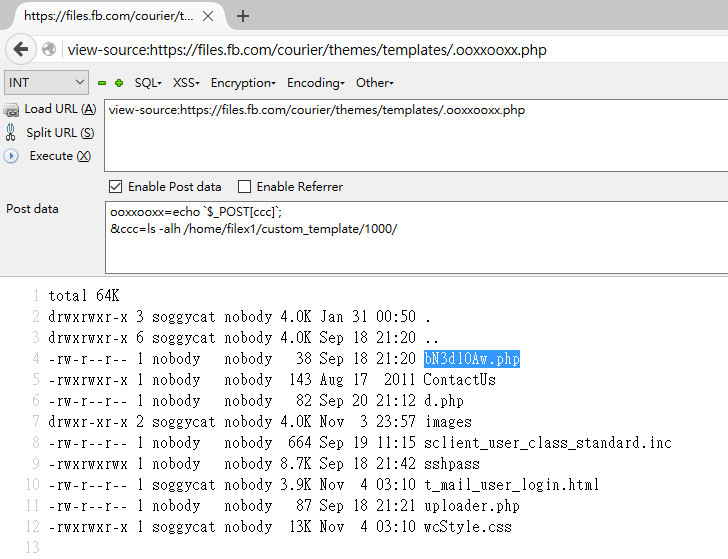
At this point, he tried to collect more data related to the alleged intrusion and discovered that the threat actor attempted to collect the login credentials of company employees who used the Accellion File Transfer Appliance.
The expert sustains that hackers used a script that had harvested at least 300 @fb.com and @facebook.com credentials in the period of time between February 1 and February 7.
By analyzing the logs he also discovered that threat actors gained access on two occasions to the system, the first time in July 2015 and later in September 2015.
The unauthorized accessed in July occurred just days before Rapid7 disclosed two vulnerabilities in the Accellion File Transfer Appliance.
Of course, there is no evidence that the intrusions were carried out by the same hacker and how the attackers breached the systems deploying the malicious webshell.
Tsai reported his discoveries to Facebook that admitted the existence of the Webshell and rewarded him with $10,000. He also reported the flaws discovered in the Accellion platform to the company.
[adrotate banner=”9″]
(Security Affairs – Facebook hacked, webshell)