
A security expert from French security outfit Sysdream, Issam Rabhi (@issam_rabhi), discovered a cross-site scripting vulnerability in Google France. Yes, you‘ve got it right, the website of the IT giant was affected by one of the most common vulnerabilities. According to the OWASP Top Ten, the cross-site scripting is the third most popular issue affecting web applications.
Such kind of flaw could be exploited by a malicious attacker for various attacks, including defacements and traffic hijacking.
“XSS flaws occur whenever an application takes untrusted data and sends it to a web browser without proper validation or escaping. XSS allows attackers to execute scripts in the victim’s browser which can hijack user sessions, deface web sites, or redirect the user to malicious sites.” reads the description provided by the OWASP TOP 10.
The experts reported the cross-site scripting vulnerability to Google on August 5th and the experts of the company fixed the vulnerability in just four days.
Rabhi published a Proof-of-concept for the attack on his website, below the exploitation step by step:
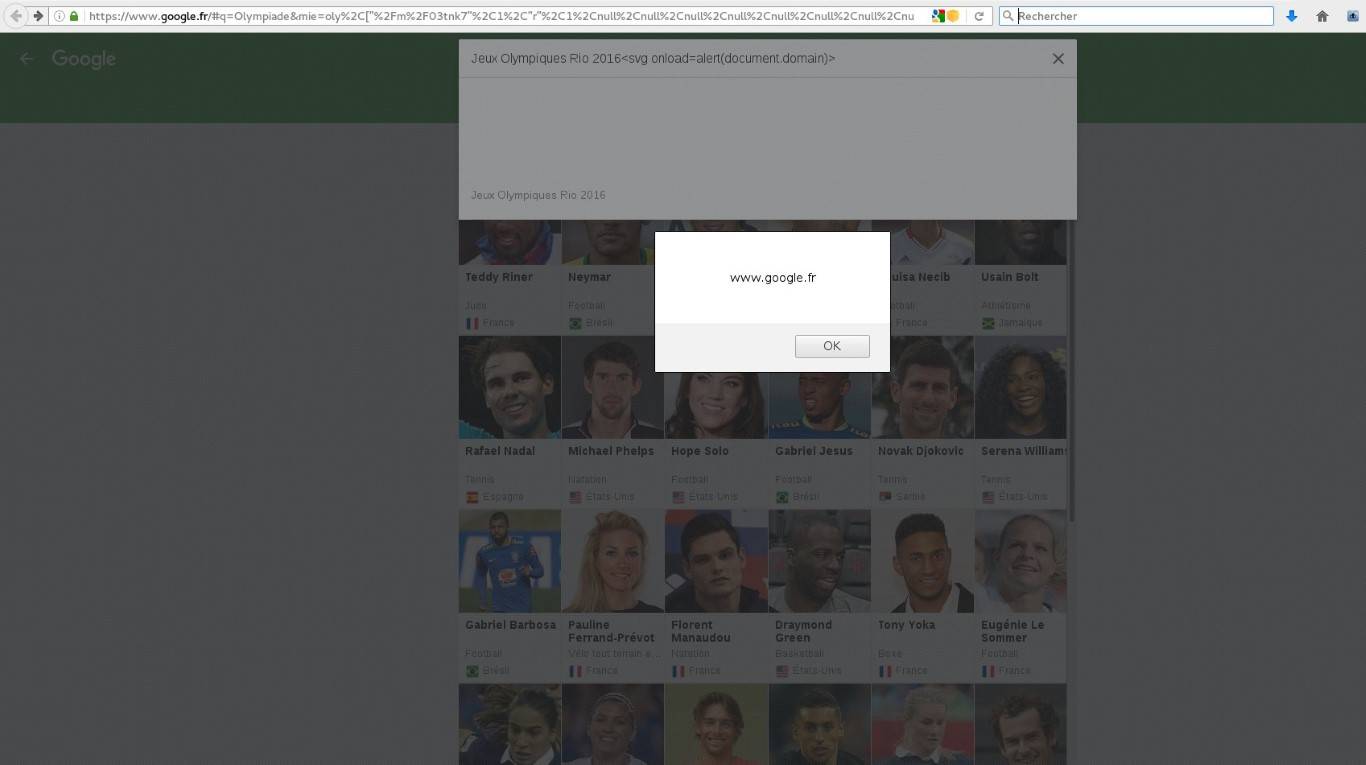
https://www.google.fr/#q=Olympiade&mie=oly%2C%5B%22%2Fm%2F03tnk7%22%2C1%2C%22r%22%2C1%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull%2C0%5D
<svg onload=alert(document.domain)>
Finally, the alert message box will pop up on the screen.
The expert did not submit the bug under the Google bug bounty program, anyway he received kudos from his colleagues.
[adrotate banner=”9″]
(Security Affairs – cross-site scripting, hacking)