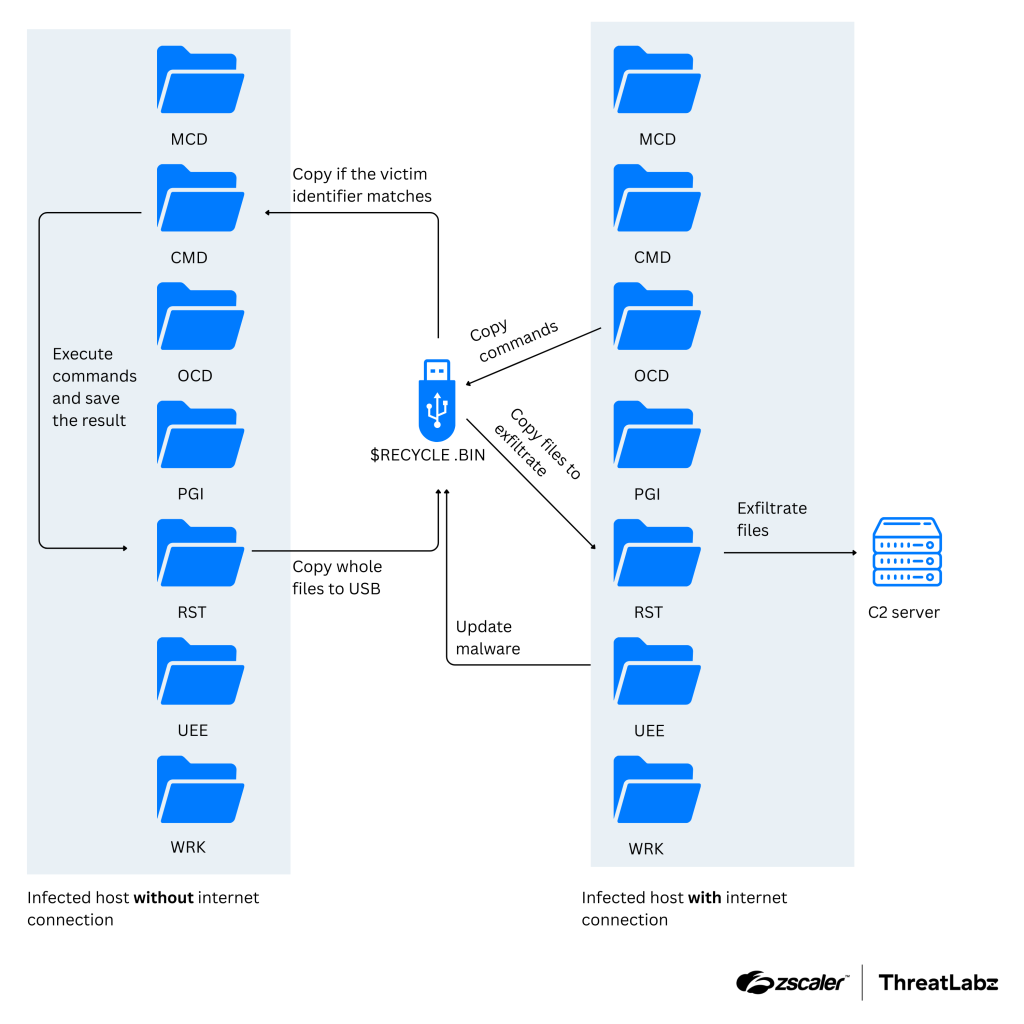
Samsung SmartThings Hub runs a Linux-based firmware and allows for communications with various IoT devices using various wireless standards Zigbee, Z-Wave, and Bluetooth.
Talos researchers explained that in order to exploit the flaws, the attacker needs to chain a number of existing vulnerabilities together.
“It is possible to gather the set of preconditions needed to exploit bugs that would otherwise be unreachable by using multiple vulnerabilities.” researchers said.
“This is commonly referred to as “chaining.” When considering the severity of vulnerabilities, it is essential to keep in mind that they might be used as part of a chain, as this would significantly elevate their severity.”
The experts identified three notable chains, only one of them is a remote code execution (RCE) vulnerability that can be exploited without prior authentication.
RCE Chain – CVE-2018-3911
This RCE chain attack affects the “video core” HTTP server of the hub, it could be exploited by attackers to inject HTTP requests into this process from a network. The flaw is an exploitable HTTP header injection bug that exists within the communications (via Port 39500) between the hub and the remote servers. The flaw could be exploited by sending specially crafted HTTP requests to vulnerable devices.
“This vulnerability is present within the JSON processing performed by the `hubCore` binary present within the SmartThings hub and could be combined with other vulnerabilities present within affected devices to achieve code execution.” states the report.
Other chains
Other chains identified by the researchers could be exploited only by an authenticated attacker.
The first attack chain is a remote code execution that could be obtained by exploiting the CVE-2018-3879 flaw that allows authorized attackers to execute SQL queries against a database running in the IoT device.
Experts noticed that chaining this flaw, with a string of other memory corruption vulnerabilities (CVE-2018-3880, CVE-2018-3906, CVE-2018-3912 to CVE-2018-3917, and CVE-2018-3919) that affects the Samsung SmartThings Hub it is possible to execute arbitrary code in the network.
Experts highlighted that the CVE-2018-3879 can also be exploited in the final chain attack for remote information leakage. This vulnerability can be used to create an empty file inside the device.
“Remote information leakage: TALOS-2018-0556 can also be used to create an empty file anywhere inside the device. As described in TALOS-2018-0593, the existence of an empty file at path “/hub/data/hubcore/stZigbee” will make the “hubCore” process to crash. Moreover, as described in TALOS-2018-0594, when the “hubCore” process crashes, it triggers an information leak that can be captured from the network.” reads the analysis tublished by Talos.
“By chaining these 3 vulnerabilities in order, an attacker can obtain a memory dump of the `hubCore` process, which contains most of the core logic, and consequent sensitive information, of the Hub.”
Talos experts tested and confirmed that the Samsung SmartThings Hub STH-ETH-250 – Firmware version 0.20.17 is affected by the flaws.
Samsung has addressed the flaw and security updates have been pushed out automatically.
“Talos recommends that these devices are updated as quickly as possible. As Samsung pushes updates out to devices automatically, this should not require manual intervention in most cases. It is important to verify the updated version has actually been applied to devices to ensure that they are no longer vulnerable. Samsung has released a firmware update that resolves these issues. An advisory related to these vulnerabilities can be found here.” concludes Talos.
| [adrotate banner=”9″] | [adrotate banner=”12″] |
(Security Affairs – Samsung SmartThings Hub, hacking)
[adrotate banner=”5″]
[adrotate banner=”13″]