
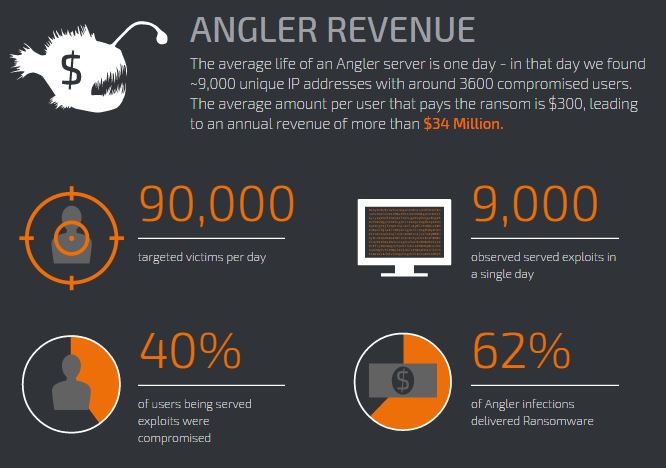
The threat landscape today is one that grows in depth and sophistication on a daily basis; however, the prevalence and effectiveness of top exploit kits found to be very active in-the-wild cannot be denied. The Angler Exploit Kit’s inner operations were recently publicly-disclosed in one of my earlier posts, revealing statistical information that suggests that the threat actors behind the Angler Exploit Kit have been profiting approximately $60 million dollars per year, from ransomware payments alone.
Although Angler may dominate the exploit kit market at this time, the Nuclear exploit kit, arguably the second most prevalent exploit kit found in-the-wild today, has recently been observed utilizing payload delivery mechanisms that are much more efficient and more sophisticated in nature than ever seen before.
Dynamic Payload Delivery, Evading Both Signature- and Heuristic-Based (or Behavior-Based) Detection
One of the primary advances made by the Nuclear EK group is that the payloads delivered by the exploit kit are dynamic in nature. While payloads were often rotated during normal Nuclear EK operation, it has been discovered that the payloads delivered by recently-analyzed hosts serving the Nuclear EK have been exceptionally volatile in nature.
Signature-based solutions detect malware based on hashes; known files, whether legitimate or nefarious in nature can be identified by their hash value (or signature). This value remains static for each file whose hash is computed utilizing the same algorithm, that contains the exact same content.
The problem with signature-based solutions is that modifying the payload and adding, removing, or flipping a few bytes will completely change the hash (signature) of the file in question, resulting in the easy evasion of solutions that are solely signature-based.
It is a known fact that relying on signature-based solutions alone is insignificant. However, the recent advancements observed being exhibited during the analysis of recent Nuclear EK activity reveal that, although each payload file appears to have the same size, the actual binary make-up of the payload files is created on-the-fly; each unique potential victim is not only just delivered a payload with an entirely different hash, but is also delivered a payload whose internal make-up, e.g. variable and function names leveraged by the payload, is entirely unique on a per-host basis (or rather, per-IP address basis).
This leads to the next point; it has been discovered that the most recent version(s) of the Nuclear EK utilizes effective techniques to evade detection, and even when it fails to exploit a target system, its anti-analysis techniques served to prevent malware analysts from re-creating and following/analyzing the infection chain employed by Nuclear.
Newer, or rather, more recent, instances of the Nuclear EK implement IP address logging capabilities; Nuclear will never deliver the same payload to an individual IP address. It has been configured to deliver malicious payloads on a per-target basis, effectively evading signature-based Anti-Virus (AV) solutions, as well as most behavioral/heuristic AV solutions.
When new functions, variables, etc. are utilized and are defined and called by a binary, that have yet to be seen before, even heuristic solutions need to take a closer look and analyze the suspect application that incorporates these never-before-seen components, to better-assess whether the file performs actions that are normal, benign, or nefarious in nature. This means that, essentially, a “patient zero” is usually required, meaning that as long as the payload file continues to be delivered as a file that is previously-unknown, the successful infection rate of the party delivering the payload will likely increase, or maintain its consistency.
Additional Evasive Techniques
Additionally, previous payloads delivered by Nuclear were recovered, extracted, and analyzed by major players in the information security field (e.g. Kaspersky). It has been reported that previously-delivered exploits have been successfully exported and analyzed by malware analysts, however, recent variants of Nuclear have been giving analysts a very hard time, and no payload/exploit has been exported and/or analyzed from the most recently-delivered Nuclear payload(s) observed in-the-wild, at this time.
About the Author Michael Fratello
Edited by Pierluigi Paganini
(Security Affairs – Exploit Kits, cybercrime)