
Original post at: https://www.qurium.org/alerts/myanmar/internet-blocking-in-myanmar-secret-block-list-and-no-means-to-appeal
In March 2020, The Ministry of Telecommunications (MoTC) issued a directive to all operators in Myanmar with a secret list of 230 sites to be blocked due to the nature of the content; adult content and fake news. The order was based on article 77 of the Telecommunications Law and the MoTC directive stipulated that the list of blocked sites was confidential and could not be made public. If an operator publicized the list, it would be in violation of the directive and local law. However, the block list included many websites that did not fall under the categories “adult content or fake news”. Several legitimate and acknowledged media related to minority ethnic groups and news focusing on the Rakhine state were found on the list.
There are four operators in Myanmar: state-owned Myanma Posts and Telecommunications (MPT), Qatar based Ooredoo, military-aligned Mytel, and privately owned Telenor Myanmar. Telenor initially challenged the blocking, and on March 23, Telenor Myanmar’s spokesperson said:
“Telenor Myanmar has not complied with the request to block sites in the category of ‘fake news’ as it has not been able to establish sufficient legal basis for this part of the request. Telenor Myanmar believes in open communication and regrets if any inconvenience is caused to the customers”
However, “dialogue with the authorities made it clear that non-compliance with the directive would have implications on the company’s ability to service the public” says Cathrine Stang Lund, Acting VP Communications at the Telenor Group, Singapore. In April 2020, Telenor complied with the directive and blocked ALL sites on the block list. In a press release from April 22, Telenor stated:
“Telenor has assessed that the risk involved in not following the directive as regards fake news is likely to have wider implications in terms of servicing the public. Hence, the remaining sites have been blocked bringing the total count to 230.”
Five months later, several legitimate and trusted news sites such as Mandalay In-Depth News, KarenNews and Voice of Myanmar, remain blocked in Myanmar.
In collaboration with the civil society organization Myanmar ICT for Development Organization (MIDO), Qurium has investigated the blocking methods implemented by Telenor Myanmar and the state-owned operator Myanma Posts and Telecommunications (MPT).
During the joint research with MIDO, traffic was recorded from Telenor (AS133385) and MPT inside Myanmar (AS9988) to a number of blocked legitimate news sites that had been classified as “fake news”. Our findings show that both Telenor and MPT block websites using DNS tampering. MPT is ignoring the DNS requests to the blocked domains, while Telenor is redirecting them to an IP address outside of the country.

The blocking mechanism of Telenor is curious and requires a bit of attention. Telenor redirects all users attempting to access a blocked domain to an inexpensive VPS outside of Telenor’s own infrastructure under a non-Telenor domain. The VPS (IP address 167.172.4{.}60) is hosted in Digital Ocean, Singapore under the domain urlblocked.pw, a domain purchased in late March 2020 for less than 2 USD.
According to Stang-Lund at Telenor Myanar, the reason for using an external domain hosted in Singapore as landing page is to protect the users. She says “this (decision) is based on a holistic evaluation, including privacy considerations, as user data on attempted access is outside of Myanmar’s jurisdiction”.
However, when redirecting blocked users to a Digital Ocean VPS in Singapore (outside of Telenor’s infrastructure), Telenor puts the readers in greater risk as the traffic leaves Telenor’s control and travels via several unknown operators. Qurium has requested a clarification from Telenor Myanmar on why Telenor did not place the block page within its own infrastructure (but outside of Myanmar’s jurisdiction), but have not received an answer.
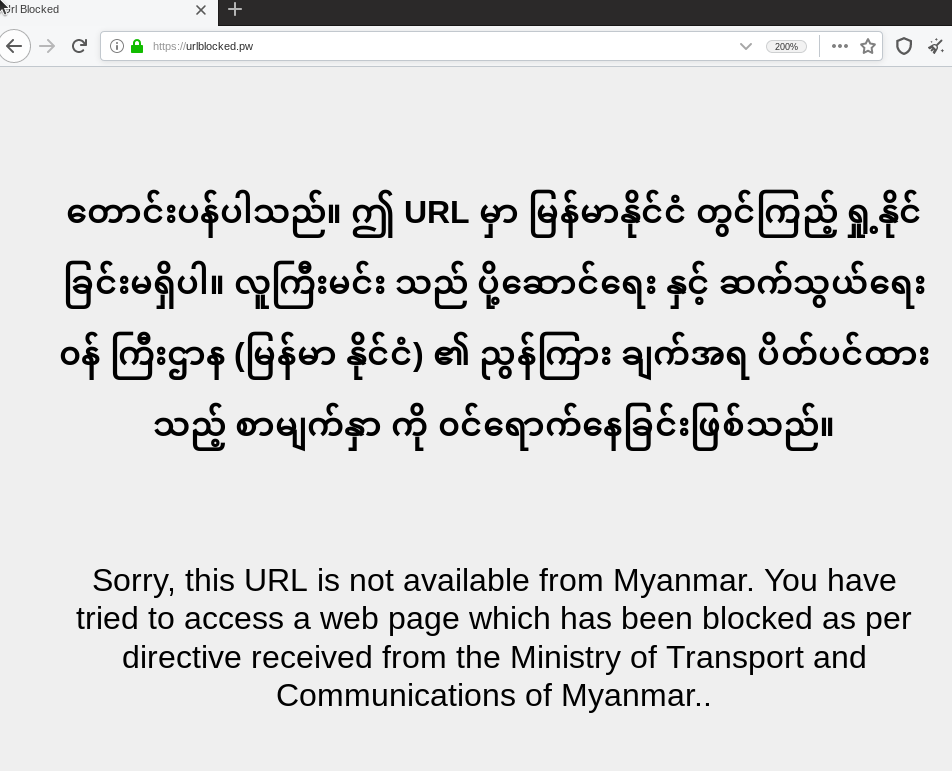
The block page provides the user a brief message in Burmese and English. The message does neither indicate that it is coming from Telenor nor provide means to appeal the blocking decision.
“Sorry, this URL is not available from Myanmar. You have tried to access a web page which has been blocked as per directive received from the Ministry of Transport and Communications Myanmar..”
Cathrine Stang-Lund explains “Since the authorities have not provided a complaint or appeal mechanism, nor contact details, Telenor Myanmar is unfortunately unable to provide that on the landing page. Any appeal should be made to the authorities.” Adding this information to the block page would increase the transparency and trustworthiness of Telenor Myanmar.
The block page uses the domain “urlblocked.pw” registered the 26th of March 2020 with a free Let’s encrypt certificate.
Domain Name: URLBLOCKED.PW Registry Domain ID: D180106494-CNIC Registrar WHOIS Server: whois.namesilo.com Registrar URL: https://www.namesilo.com Updated Date: 2020-03-31T03:01:23.0Z Creation Date: 2020-03-26T02:55:00.0Z Registry Expiry Date: 2021-03-26T23:59:59.0Z Registrar: NameSilo, LLC
To confirm the domain ownership, Qurium tried to reach the domain owner via an online form provided by nic.pw. A month later, no response has been provided.
The mail account [email protected], published as contact details in DNS, bounces all incoming mails.
There are several aspects of the Internet blocking in Myanmar that raise questions. In this section we have collected the open questions that still are unanswered.
To circumvent Internet blocking of legitimate news sites, human rights organizations and LGBTQI initiatives, Qurium has developed the mirroring service Bifrost. Bifrost creates live-mirrors of WordPress sites, and pushes the content to large cloud storage services like Google or Amazon, which are too expensive for governments to block. In the case of Myanmar, Qurium has chosen to mirror In-Depth News Mandalay, a legitimate local news site focusing on the Mandalay region. The news site was blocked in March 2020 under the category “fake news”, after being openly critical against military violence and government corruption.
For further reading on current situation of Internet blocking in Myanmar, we recommend the article “Myanmar blocks websites amid COVID19” published by OONI in May 2020.
About the author:
About the authors – Contacts:
Forensic report: Tord Lundström, Qurium Media Foundation < [email protected] >
Media: Clara Zid, Qurium Media Foundation < [email protected] >
| [adrotate banner=”9″] | [adrotate banner=”12″] |
(SecurityAffairs – hacking, Myanmar)
[adrotate banner=”5″]
[adrotate banner=”13″]