
A remote simple hack devised by a group of security researchers threatens an amazing number of Android and iOS apps. An attacker can use the technique to sign into any victim’s mobile app account without any knowledge of the legitimate user.
The research team from the Chinese University of Hong Kong is composed of Ronghai Yang, Wing Cheong Lau, and Tianyu Liu. The experts discovered that the vast majority of popular mobile apps that use the single sign-on (SSO) service doesn’t properly implement the OAuth 2.0 protocol.
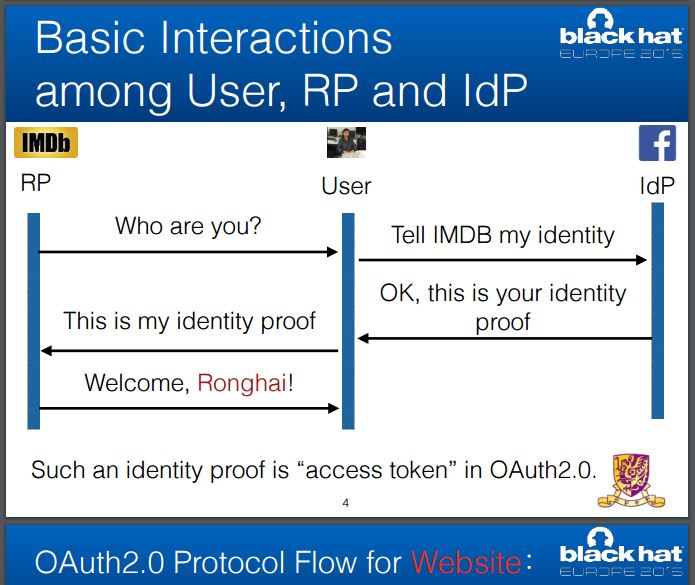
The OAuth 2.0 authentication protocol is widely used on social networking sites, every day billion of users access their profiles on Facebook and Google+ using it.
Using the OAuth 2.0, users can sign in for third-party services by verifying existing identity through their accounts on popular web services such as Google, Facebook, or Sina.
Once authenticated, the users haven’t to provide their credentials to access other services implementing the OAuth 2.0 protocol.

“The problem is a pretty basic mistake,” Lau told Forbes.
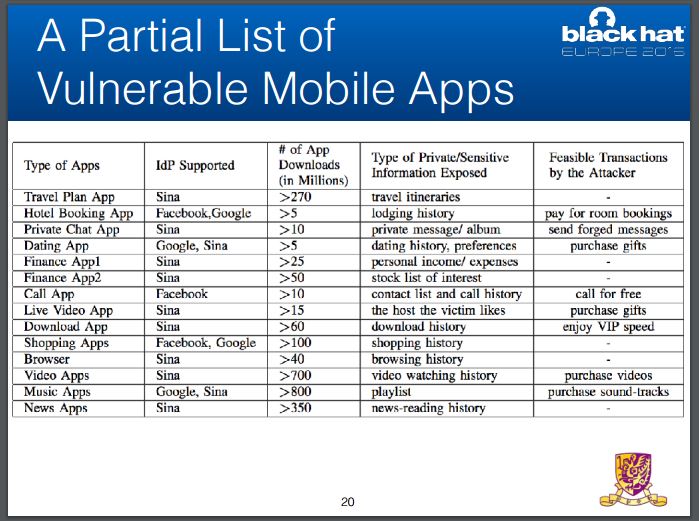
“The impact, he said, could be severe. For instance, if the hacker broke into a travel app, they could learn the full itinerary of an individual. For a hotel booking app, they could book a room and have the victim pay for it. Or they could simply steal personal data, like addresses or bank details.” wrote Thomas Fox-Brewster from Forbes.
“A lot of third party developers are ma and pa shops, they don’t have the capability. Most of the time they’re using Google and Facebook recommendations, but if they don’t do it correctly, their apps will be wide open.” .
The experts have found hundreds of popular US and Chinese Android apps that support SSO service. The number of downloads is huge, the researchers explained that a total of over 2.4 Billion downloads are vulnerable to this attack.
The experts estimated that over a Billion different mobile app accounts are at risk of being hijacked with their attack.
The researchers did not perform any test on iOS devices, but they believed that the attack would work also on Apple apps
“Although our current attack is demonstrated over the Android platform, the exploit itself is platform-agnostic: any iOS or Android user of the vulnerable mobile app is affected as long as he/ she has used the OAuth2.0-based SSO service with the app before,” the researchers said.
[adrotate banner=”9″]
(Security Affairs – oAuth 2.0, mobile hacking)