Ransomware is one of the cyber threats that has created major problems last year, with increasing frequency cyber criminals gangs have opted for an extortion scheme to immediately monetize their efforts. Security expert have observed a surge in the number of infections related to ransomware, Cryptolocker is the most popular malicious agent which targeted millions of computers worldwide despite many others varianta were discovered in the wild. “Ransomware attacks grew by 500 percent in 2013 and turned vicious” according 2014 Internet Security Threat Report (ISTR), which provides a detailed analysis of the techniques adopted by cybercriminals to conduct sophisticated and dangerous malicious campaign.  Experts at Trendmicro have proposed in their quarterly threat roundup an analysis of different ransomware variant which perform additional routines to comprimise victim’s machine, some of them for example are able to stealing cryptocurrency wallets from the PC, other to steal local documents.
Experts at Trendmicro have proposed in their quarterly threat roundup an analysis of different ransomware variant which perform additional routines to comprimise victim’s machine, some of them for example are able to stealing cryptocurrency wallets from the PC, other to steal local documents.
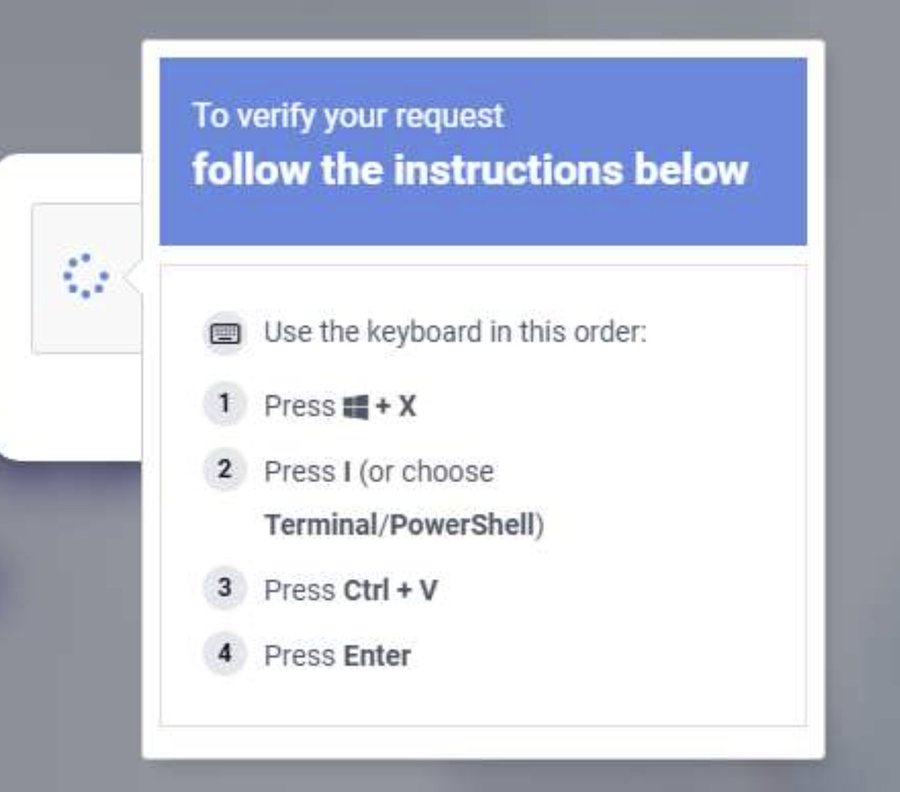
The experts recently encountered a variant, dubbed TROJ_POSHCODER.A, that uses the Windows PowerShell feature to encrypt victim’s files with Advanced Encryption Standard (AES). Bad actors use WindowsPowershell to implement detection avoidance techniques, however, once discovered the use ofPowerShell, decrypting and analyzing this malware was not too difficult.
“Since it uses Powershell, TROJ_POSHCODER.A is script-based, which is not common for ransomware. It uses AES to encrypt the files, and RSA4096 public key cryptography to exchange the AES key. When executed, it adds registry entries, encrypts files, and renames them to {filename}.POSHCODER. It also dropsUNLOCKYOURFILES.html into every folder. Once all files on the infected system are encrypted, it displays the following image.”
“Windows PowerShell is a task automation and configuration management framework from Microsoft, consisting of a command-line shell and associated scripting language built on the .NET Framework. PowerShell provides full access to COM and WMI, enabling administrators to perform administrative tasks on both local and remote Windows systems as well as WS-Management and CIM enabling management of remote Linux systems and network devices.” (Wikipedia)
TROJ_POSHCODER.A is a script-based ransomware, it uses RSA-4096 public key cryptography to exchange the AES key with the victims in order to decrypt the files. The instruction proposes by TROJ_POSHCODER.A Ransom note redirect users to another page asking victims to download the Multibit application to have their own Bitcoin-wallet account for 1 Bitcoin. Victims fill the form providing email address, BTC address and ID, as a result to get decryption keys. The TROJ_POSHCODER ransomware has primarily affected users in the United States. 
Be aware, cyber criminals are adopting techniques even more sophisticated to deceive their victims.
| [adrotate banner=”9″] | [adrotate banner=”12″] |
(Security Affairs – TROJ_POSHCODER, ransomware)
[adrotate banner=”5″]
[adrotate banner=”13″]