
The ethical hacker Ryan Pickren demonstrated that it is possible to hack Apple iPhone or MacBook users by simply tricking them into visiting a website with the Safari browser.
Pickren reported seven vulnerabilities to Apple that rewarded him with a $75,000 bounty.
Turns out merely visiting a website — not just malicious but also legitimate sites unknowingly loading malicious ads as well — using Safari browser could have let remote attackers secretly access your device’s camera, microphone, or location, and in some cases, saved passwords as well.
The company addressed the issues with security updates included in Safari versions 13.0.5 (January 28, 2020) and Safari 13.1 (March 24, 2020).
“Some quick research shows that Safari keeps track of permission settings on a per-website basis to let websites access sensitive content such as GPS location or camera “without always asking for permission.” Basically, you can allow Skype to access your camera whenever it wants because you trust Skype. You can see which websites you currently trust in Safari > Preferences > Websites.” wrote the expert.
The expert demonstrated that chaining three of the Safari flaws he discovered it was possible to allow malicious sites to impersonate any legit site that was trusted by the victims. This means that an attacker exploiting the three flaws could have allowed accessing the camera or microphone by abusing the permissions granted by the victim to the trusted domain only.
The hack is possible because the Safari browser grants access to specific permissions (i.e. camera, microphone, location) to each individual website. If a website is authorized to access to the camera and the microphone, such as Skype or Zoom, attackers could impersonate them to access to the same privileges.
“But there is an exception to this rule. Apple’s own apps get camera access for free. So Mobile Safari can technically access the camera without asking.” continues the experts. “Furthermore, new web technologies such as the MediaDevices Web API (commonly used in WebRTC transmissions) allow websites to utilize Safari’s permission to access the camera directly. Great for web-based video conferencing apps such as Skype or Zoom.”
The expert pointed out that the URL’s scheme is completely ignored and this could represents a source of problems because some schemes don’t contain a meaningful hostname at all, such as file:, javascript:, or data:.
The expert noticed that Safari failed to use origins to keep track of your “currently open websites” granting access to a different site that shouldn’t have obtained permissions. This could have allowed granting access to a malicious website the same permissions of a legitimate one.
Experts demonstrated that it was possible to use a “file:” URI (e.g., file:///path/to/file/index.html) to fool the browser into changing the domain name using JavaScript.
“The page actually accepted this URI as valid and reloaded the same content. Which means I just changed the document
“Sure enough, Safari thinks we are on skype.com and I can load some evil JavaScript. Camera, Microphone, and Screen Sharing are all compromised when you open my local HTML file. Bonus – Safari also seems to use this lazy hostname parsing method to fill autocomplete on passwords. So I can steal plaintext passwords if you accept autocomplete.”
The expert also demonstrated how to exploit a “blob:” URI (e.g. blob://skype.com) to run arbitrary JavaScript code, for example, to access the victim’s webcam without permission.
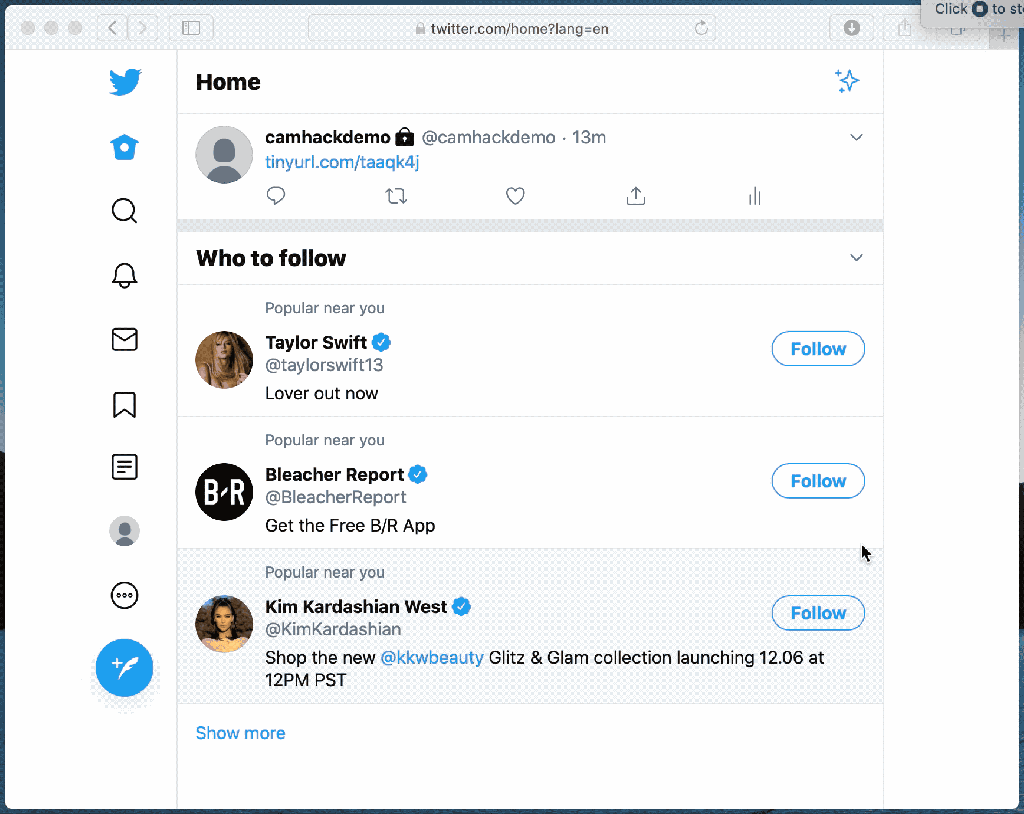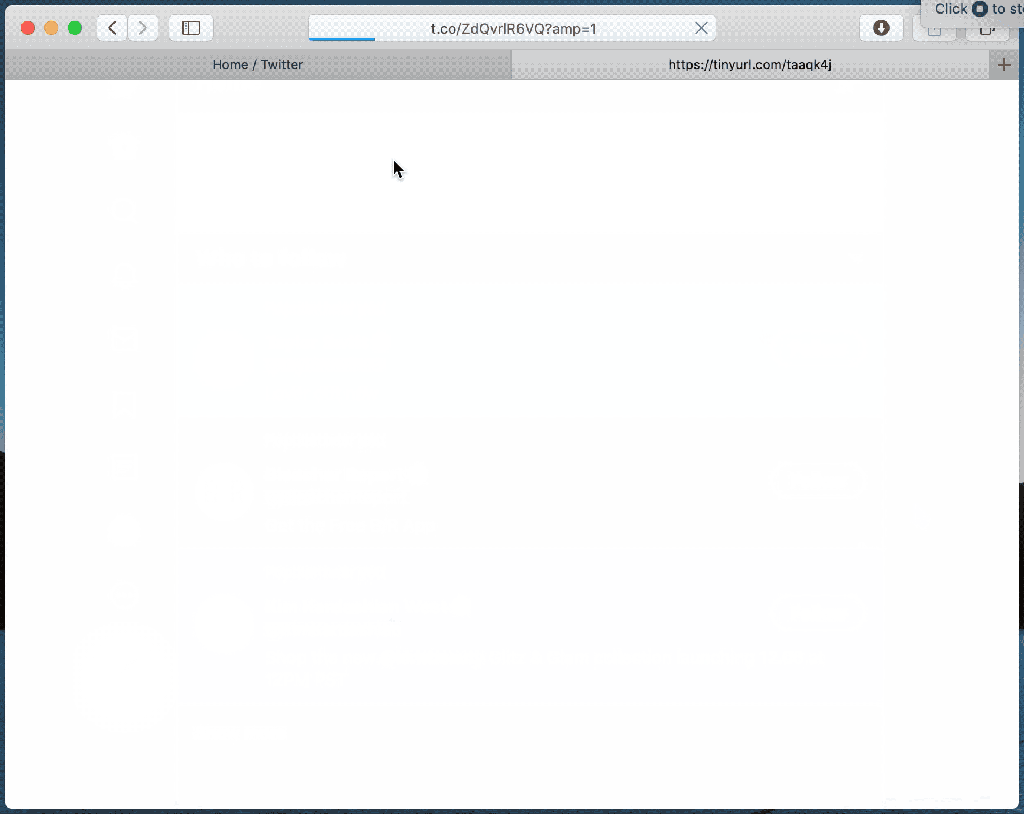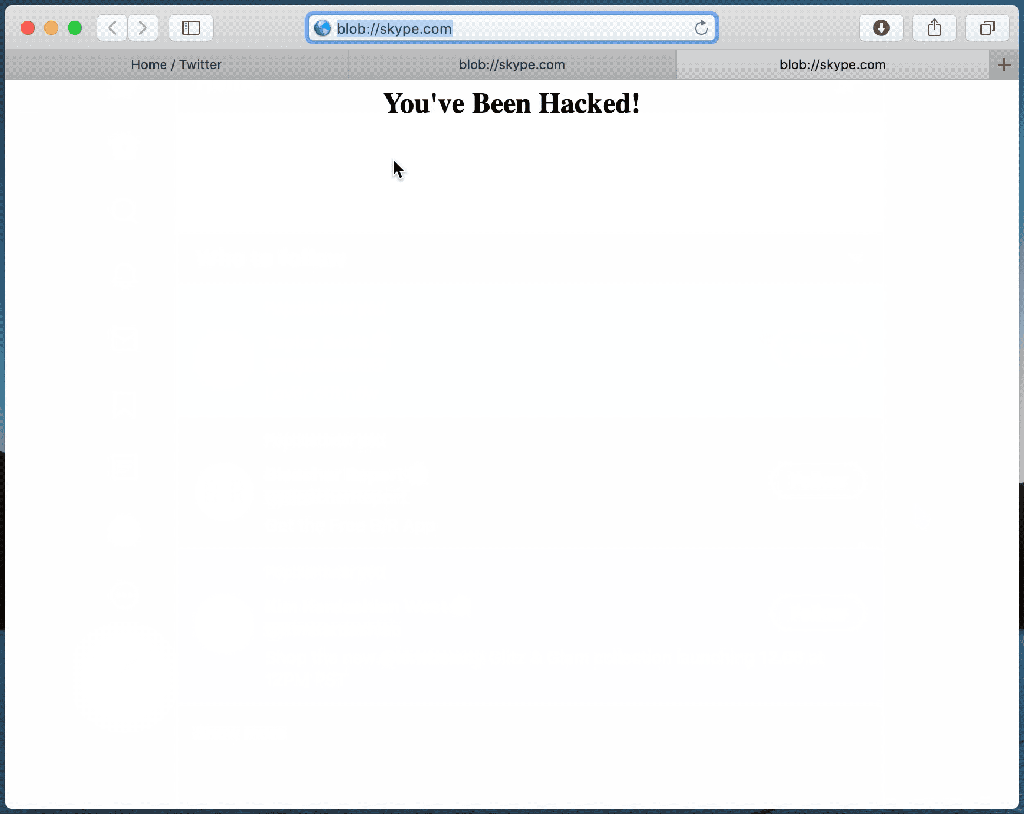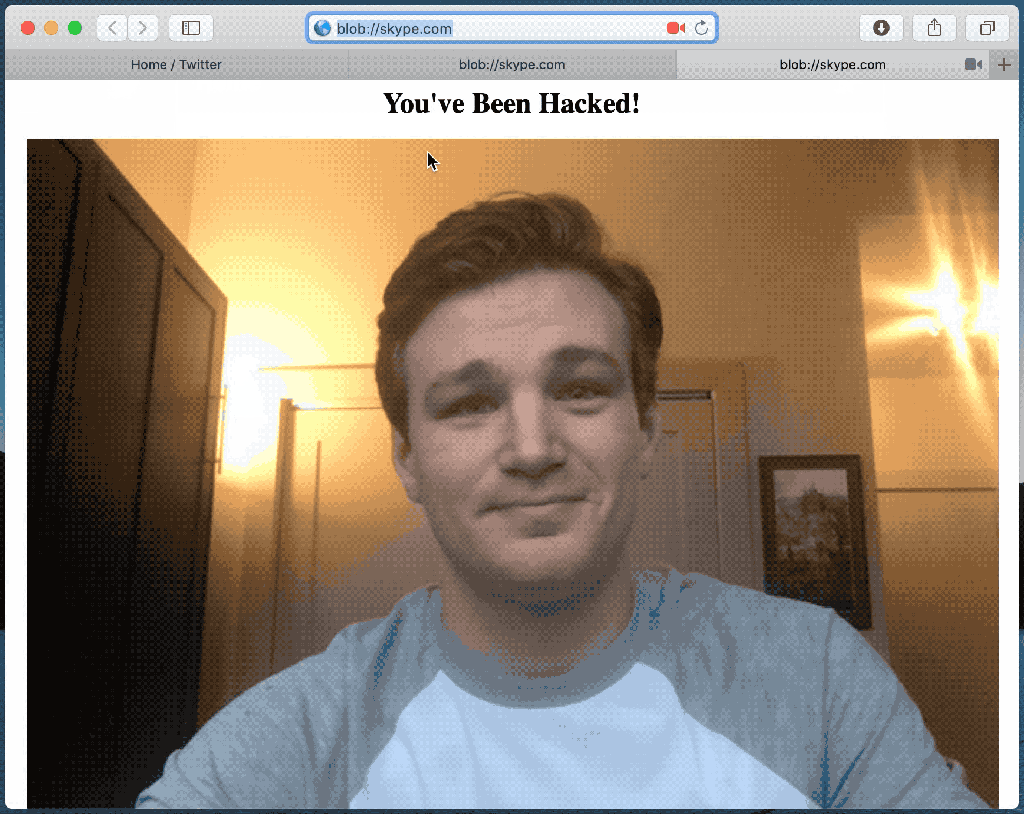
Technical details about the hack demonstrated by the researchers are included in his post.
Apple users should keep their browsers up-to-date.
| [adrotate banner=”9″] | [adrotate banner=”12″] |
(SecurityAffairs – hacking, Apple iphone)
[adrotate banner=”5″]
[adrotate banner=”13″]