
The phishing is still a very profitable technique for crooks, phishers try to improve old tactic in a new fashion in order to steal victims’ information.
One of the most common suggestions to mitigate phishing attacks is to inspect the links in a mail to see if they reference to the website where you would expect them to point. Although good advice, this is NOT a guarantee that you are going to be safe.
Unfortunately, this is not enough to protect users, It is important never follow the URLs included in the emails or attachments.
The security expert and malware researcher @dvk01uk reported a very unusual phishing attack on PayPal leveraging on Javascript to send the user to the promised PayPal site while their login credentials are being sent to an entirely different domain.
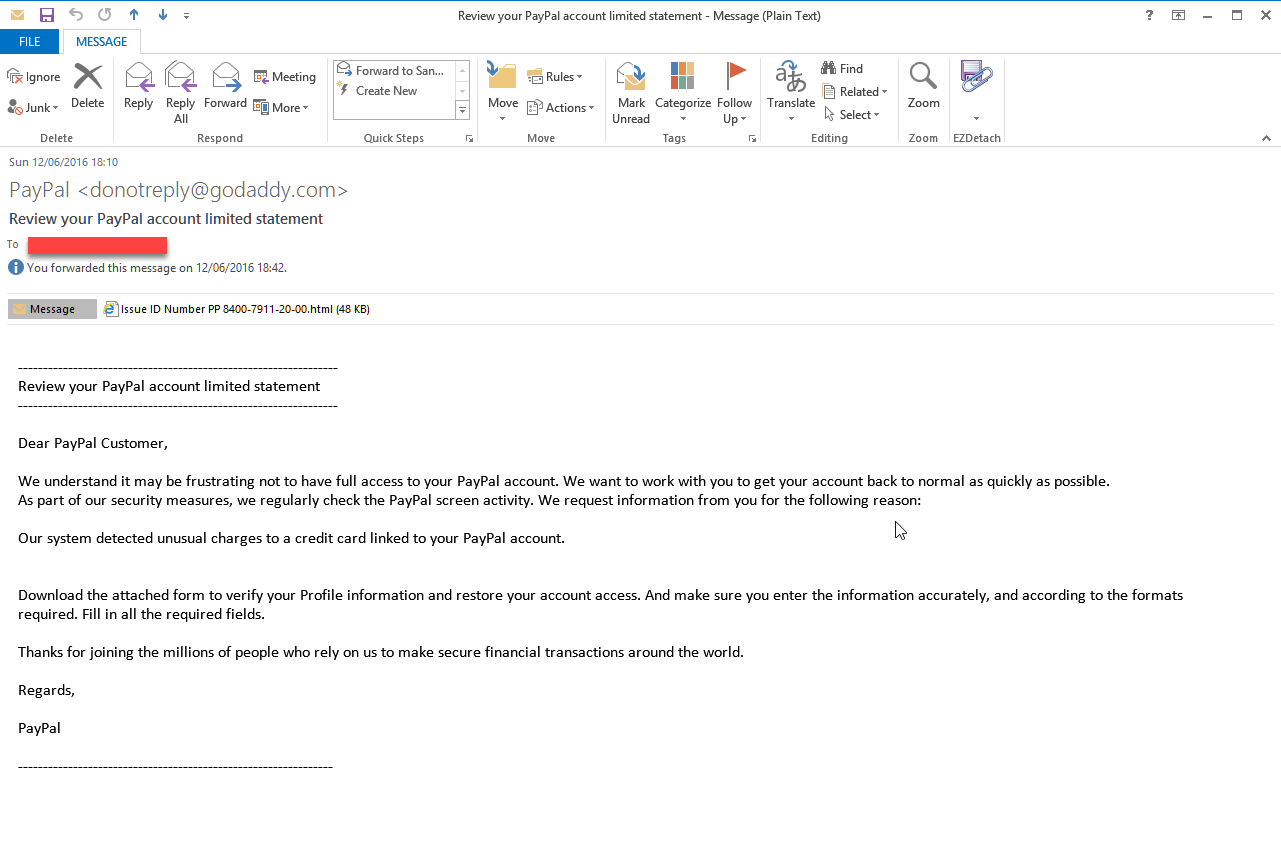
“The phishers are using a hidden JavaScript redirect method to steal the data, while the submit button still shows as going to PayPal.com. This is extremely dangerous and very difficult for an average user to defend against and know that they are passing information to a criminal.” wrote the expert. “We always tell users to hover the mouse over a link or submit button and make sure that the link is to the correct “safe” location. This no longer is safe advice when hidden JavaScript redirection is used. “
The Javascript is able to intercept any interaction with PayPal.com and hijack them to the phishing page. The submit button goes to the legitimate PayPal WebSite avoiding to raise suspicious, but a javascript running on the page intercepts all posts to PayPal.com and diverts them to the actual phishing page to accept all victim’s details, while his browser still goes to the genuine PayPal page.
“The javascript runs as soon as the page (HTML attachment) is loaded and intercepts all posts to PayPal.com and diverts them to the actual phishing page to accept all your details, if you are unwise enough to fall for this trick.” continues the expert.

The phishing page used in the attack spotted by the researchers is hosted on www[dot]egypt-trips[dot]co which seems to be an unused website running a WordPress CMS.
This technique could be very insidious if the attackers also hosted the phishing page on a website that appears as legitimate, for example http://paypalnew.com.
“Now if the phishers were intelligent enough to put this on a website with a half believable URL, something like http://paypalnew.com which was used in a series of Phishing attacks yesterday, we would be in trouble, because users wouldn’t realise that they were giving their details to a phisher.
Luckily enough, there are enough warning bells with this particular one to prevent most people falling for it, but some always do.” closes the post.
In this specific case, the site owner was already contacted by the expert.
[adrotate banner=”9″]
(Security Affairs – Phishing, PayPal)