
Security experts from Kaspersky Lab revealed that the
In February, malware researchers at Carbon Black spotted a new strain of the Shlayer malware that was targeting MacOS versions from 10.10.5 up to 10.14.3.
The malware was posing as an Adobe Flash update and it was distributed through a large number of websites, fake or compromised legitimate domains.
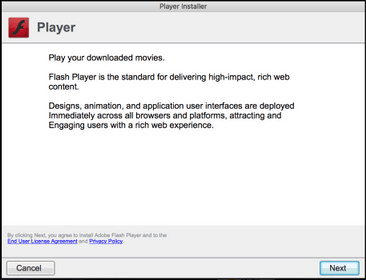
This variant of the Shlayer malware employs multiple levels of obfuscation, experts discovered that many of the initial DMGs are signed with a legitimate Apple developer ID.
The malware installs Any Search bar on the targeted Mac device to deploy adware, it also intercepts and collects browser data and it is able to alter search results to deliver malicious ads.
According to Kaspersky, in 2019, one in ten of our Mac security solutions encountered this malware at least once.
“For close to two years now, the Shlayer Trojan has been the most common threat on the macOS platform: in 2019, one in ten of our Mac security solutions encountered this malware at least once, and it accounts for almost 30% of all detections for this OS.” reads the analysis published by Kaspersky. “The first specimens of this family fell into our hands back in February 2018, and we have since collected almost 32,000 different malicious samples of the Trojan and identified 143 C&C server domains.”

The malware was used to deliver multiple adware including AdWare
Experts pointed out that the infection process of Shlayer malware hasn’t changed over the time and the malicious code has remained active throughout 2019.
Unlike other Bash-based
“The negative consequences for the user can be seen by investigating the AdWare
The researchers detailed one of the extensions downloaded and installed by the malware that is called
Most Shlayer infection attempts were observed in the U.S.
“Having studied the Shlayer family, we can conclude that the macOS platform is a good source of revenue for cybercriminals.” concludes the report. “The Trojan links even reside on legitimate resources — attackers are adept in the art of social engineering, and it is hard to predict how sophisticated the next deception technique will be.”
| [adrotate banner=”9″] | [adrotate banner=”12″] |
(
[adrotate banner=”5″]
[adrotate banner=”13″]