
Cyber criminals continue to use compromised websites to serve malware or to redirect visitors to domains hosting exploit kits.
Experts at Malwarebytes observed a new attack pattern that relies on a domain name to lure owners of websites into thinking it is a component of social plugins or a widget.
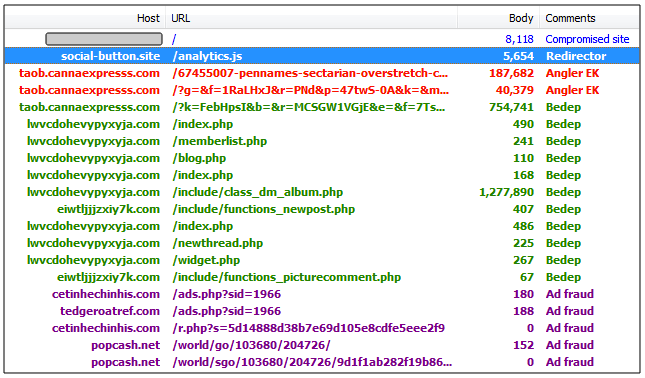
“Rather, this one uses a domain name used to lure website owners into thinking this is part of social plugins or such widget: socialbutton[.]site. Those buttons typically allow users to ‘Like” or retweet an article easily from the website they are visiting.” states a blog post published by MalwareBytes.
The researchers discovered two JavaScript files (analytics.js and widget.js) used by crooks, each of them has a clean version and a malicious one.
Users are served the malicious version only when they land on the website with the proper referer (compromised upper site).
The experts have analyzed the Injected script and obfuscated code gathering evidence of a redirection to the Angler exploit kit. The analysis of the domain hosting the Angler EK allowed the experts to confirm its fraudulent purpose.

Domain: social-button.site Registrar: Namecheap INC Email: [email protected] Country: Panama Create Date: 2016-04-13T19:39:57
The Angler Exploit Kit was used by crooks to serve a fileless variant of the Bedep malware.
Experts at Malwarebytes highlight that the hacking campaign mainly targeted poorly configured and outdated websites that were breached via automated attacks.
Recently security experts spotted a large number of attacks relying on exploit kits (e.g. Neutrino Exploit Kit, Angler Exploit kit, Rig Exploit Kit) installed on websites running popular CMS such as Joomla and WordPress.
[adrotate banner=”9″]
(Security Affairs – Angler Exploit Kit, cybercrime)