“Facebook Notes allows users to include <img> tags. Whenever a <img> tag is used, Facebook crawls the image from the external server and caches it. Facebook will only cache the image once however using random get parameters the cache can be by-passed and the feature can be abused to cause a huge HTTP GET flood.”
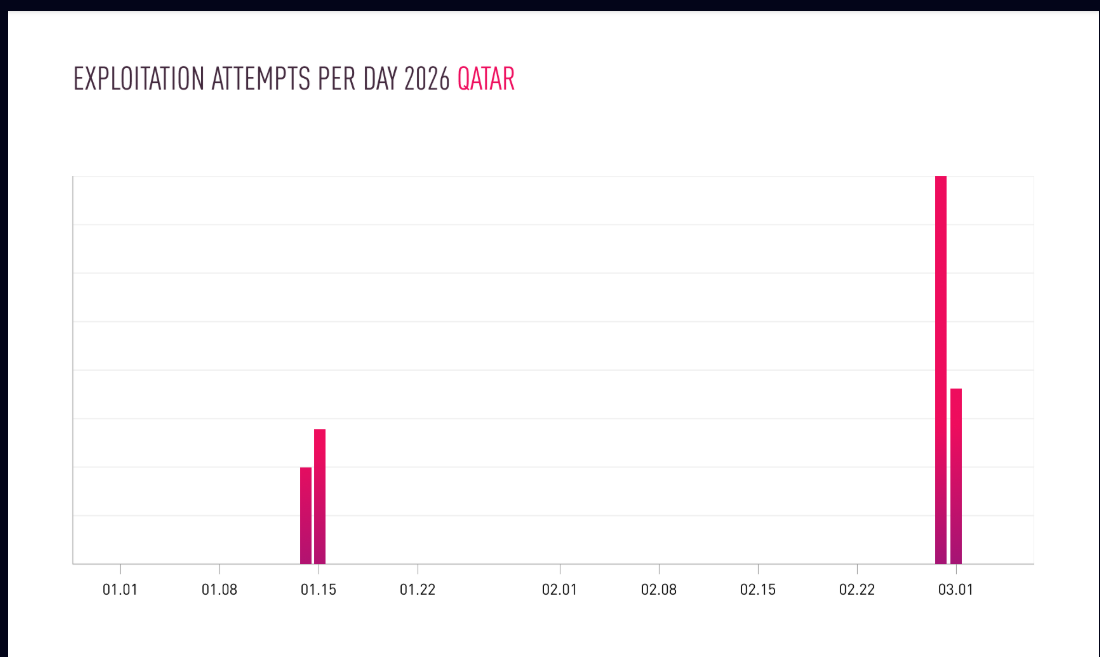
Facebook servers are forced to download 1 MB of file 1000 times in one page view (It has been estimated that each note is now responsible for 1000+ http requests). If 100 Facebook users are reading the same note at the same time, then Facebook servers will be forced to download 1 x 1000 x 100 = 100,000 Mb or 97.65Gb bandwidth within few seconds from the targeted servers. In the image below is reported the graph for the 400 Mbps traffic generated from 127 Facebook servers in the proof-of-concept made by Thapa by attacking on his own web server.
Following the description provided in the post by the Chaman Thapa.
Steps to re-create the bug as reported to Facebook Bug Bounty on March 03, 2014. Step 1. Create a list of unique img tags as one tag is crawled only once
<imgsrc=http://targetname/file?r=1> </img><imgsrc=http://targetname/file?r=1></img> ..<imgsrc=http://targetname/file?r=1000></img>
Step 2. Use m.facebook.com to create the notes. It silently truncates the notes to a fixed length.
Step 3. Create several notes from the same user or different user. Each note is now responsible for 1000+ http request.
Step 4. View all the notes at the same time. The target server is observed to have massive http get flood. Thousands of get request are sent to a single server in a couple of seconds. Total number of facebook servers accessing in parallel is 100+.
“A scenario of traffic amplification: when the image is replaced by a pdf or video of larger size, Facebook would crawl a huge file but the user gets nothing.” “Each Note supports 1000+ links and Facebook blocks a user after creating around 100 Notes in a short span. Since there is no captcha for note creation, all of this can be automated and an attacker could easily prepare hundreds of notes using multiple users until the time of attack when all of them is viewed at once.” noted Chaman Thapa.
“In the end, the conclusion is that there’s no real way to us fix this that would stop attacks against small consumer grade sites without also significantly degrading the overall functionality,” replied Facebook to the researcher.
(Security Affairs – Facebook, DDoS)