
But what does Apple’s iPhone have to do with it??
Well, keep on reading… (
Some time ago, me and my “business partner” @padovah4ck, were looking for possible privileged file operations exploitable via hardlinks.
At some point, the directory c:\programdata\apple\lockdown caught our attention.
This folder is used by the “Apple Mobile Device Service” which is installed

As you can see below, standard users can add files in this directory:

Each time a new device is plugged in, the driver will write a “pairing certificate” file in this directory in the form of <UDID>.plist, where UDID is the universal Id of the Apple device.
So let’s plugin our Apple device. A “pairing certificate” will be generated and the permissions set on this file are the following:
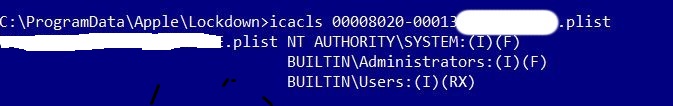
As you can see, users have only read access to this file.
But now comes the funny part. If you unplug the device and then plugin again, some “magic” happens, granting to users Full Control over that file:

We observed this “strange” behavior using the “procmon” tool from Sysinternals:

A SetSecurity call is made from an elevated context (SYSTEM) and will grant full control to users on the resource. So the question is, can this operation be exploitable?
Yes!! You got it, enter “NATIVE HARDLINKS“…
Standard Windows users do not need special privileges to create this type of links and we can use Forshaw’s utilties to manage them.
So why not setting a “native hardlink” on this file and let him point to a resource where only SYSTEM has full control?
This is what we are going to do, setting a hardlink from our <udid>.plist file to license.rtf located in System32 folder:

Now we just need to plugin our Apple device in order to alter the permissions on destination file:

And yes, it works!
At this point we have all the pieces of the puzzle, we only need to change the destination file to printconfig.dll, then overwrite it with our own dll, start the XPS print job and finally enjoy the SYSTEM shell (this exercise is left to the reader) 😉
Here you can watch a video of the POC.
Generic
Original post available at the following URL:
https://decoder.cloud/2019/12/12/from-iphone-to-nt-authoritysystem/
About the authors
Andrea Pierini (@decoder_it)
“Andrea is an IT Architect & Security Manager with long-term experience and in-depth knowledge covering all aspects of IT: from SW development to systems administration; networking administration and IT security. He can define himself “security enthusiast”, interested in all emerging technologies in offensive and defensive security. He likes writing and speaking about IT security and bug hunting. Cycling and addicted”
Christian Danieli (@padovah4ck)
“Chris is an “old-school” developer turned into Security Engineer and Automation Operator. He still codes a lot and has an innate ability to find bugs and solve problems. He saw and explored almost everything an IT guy could have seen since 1995. OS Windows Lover especially for the bug hunting part! Fishing and
| [adrotate banner=”9″] | [adrotate banner=”12″] |
(
[adrotate banner=”5″]
[adrotate banner=”13″]